Admin By Request
Admin By Request
Georgia College Division of Information Technology has implemented Admin By Request to comply with security requirements established by the University System of Georgia. Admin By Request is a service that allows you to easily request administrative access from your computer. Whenever administrative rights are required to perform an action on your computer, you will be prompted to fill out a short form and a request will automatically be sent to the IT Help Desk. The IT Help Desk staff will review the request and either approve or provide feedback so you can continue with the task. Please be aware, actions performed during an admin session will be logged.
Prerequisites:
The Admin By Request client must be installed on the computer to allow admin access requests. If Admin By Request is not installed on your computer, please submit an IT Help Desk ticket.
To confirm that Admin By Request is installed on your machine, look for the Admin By Request check mark in the Task Bar on Windows or the Applications folder on a Mac.
Windows:
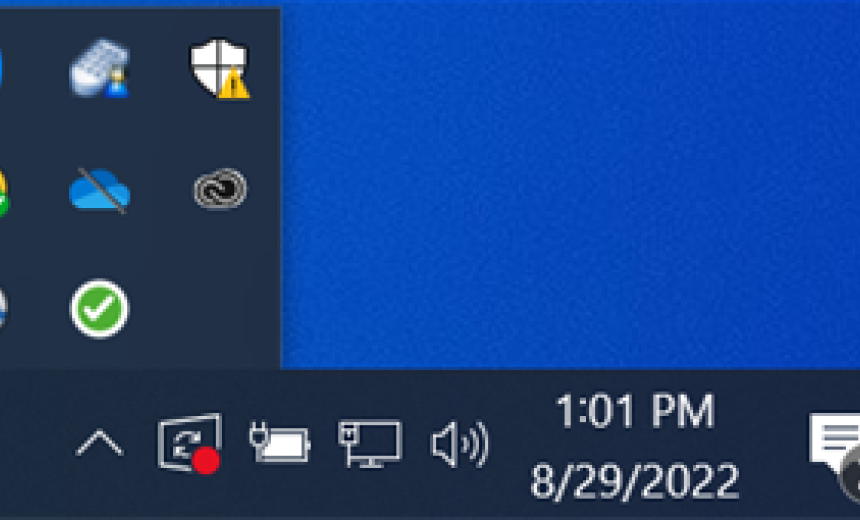
Mac:
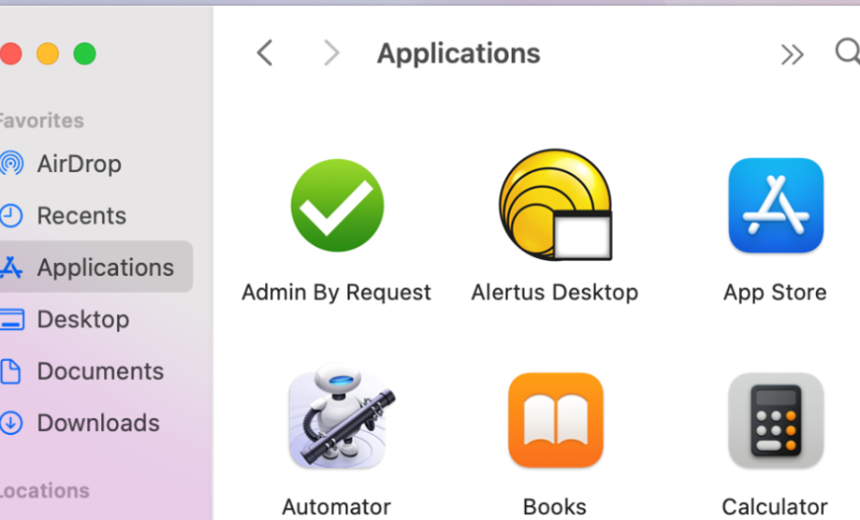
Instructions:
Admin by Request Instructions - Windows
Campus Site Licenses
- Acrobat X Pro for Creative Suite
- Adobe Audition CS6
- Adobe CS6 Master Collection
- Adobe Prelude CS6
- Adobe Premier Pro CS6
- After Effects CS6
- Bridge CS6
- Cisco Jabber C 10.6
- Cisco VPN Client (enables secure access to remote resources)
- Dreamweaver CS6
- Encore CS6
- Endnote X7 (research/bibliography software)
- Fireworks CS6
- Flash Builder
- Flash Professional CS6
- Illustrator CS6
- InDesign CS6
- Media Encoder CS6
- Photoshop Extended CS6
- Respondus (Exam creation and management)
- Sanako Student Recorder
- SoftChalk 9
- SOLO 6
- SpeedGrade CS6
- SPSS 25
Center for Teaching and Learning
Link to Resources provided by CTL.
Classroom Technology - Technology Enhanced Collaboration
GCSU has implemented the use of Infocus LiteShow4 branded as Technology Enhanced Collaboration (TEC) on the wall control in the classroom. TEC allows several devices to connect.
TEC is available in the following classrooms:
- A&S 115,138, 140, 165, 167, 236, 238, 240, 242, 251, 270, 272, 274, 275, 336, 338, 342, 348, 364, 366, 368 and 370
- Atkinson 106, 107, 108 and 109
- Chappell 113
- Ennis Hall 20, 105 and 217
- Health Sciences 202,207 and 300
- Herty Hall 249, 250, 252, 304 and 308
- Kilpatrick 125, 224, 226 and 227
- West Campus 101
TEC Instructions Updated (PDF)
HEOA Compliance Procedure - Copyright
The Higher Education Opportunity Act (HEOA) includes provisions to reduce illegal sharing of copyrighted material through peer-to-peer (P2P) file sharing. HEOA requires institutions to:
- Make an annual disclosure to students that the illegal distribution of copyrighted material may subject them to criminal and civil penalties and describes the steps the institution will take to detect and punish illegal distribution of copyrighted materials
- Certify that the university has developed plans to effectively combat the unauthorized distribution of copyrighted material including the use of one or more technology-based deterrents
- Offer legal alternatives to illegal file sharing to the extent practical
- Identify procedures for periodically reviewing the effectiveness of the plans to combat the unauthorized distribution of copyrighted materials.
Annual Disclosure
Georgia College uses a wide variety of methods to inform students about copyright laws, including:
- Each year the Office of Information Security at Georgia College sends out an email to all student email accounts regarding copyright laws and campus policies related to violating copyright laws.
- All students are required to adhere to practices stated in the “General Acceptable Use of Technology Policy”. All residential students must also adhere to the practices stated in the “RESNET Acceptable Use Policy”. Both policies are published in the GC Policy Manual and posted on the University’s website.
Plan to Combat Unauthorized Distribute of Copyrighted Material
Georgia College uses several technology-based deterrents to combat the unauthorized distribution of copyrighted materials, including:
- GCSU utilizes Packet Shaping that allows the campus to ensure smooth flow of content to and from the internet with the ability to prioritize traffic based upon need or policy. This technology also allows for Dynamic Partitioning which gives the network administrator the ability to isolate large bandwidth users and abusers. When a high-bandwidth consumption is observed, the user is contacted to ensure that the purpose of usage is legitimate.
- GCSU limits identifiable P2P traffic to only a very small percentage of the overall network capacity making it slow enough to be a deterrent.
- GCSU blocks all known illegal P2P traffic.
- GCSU’s policies and procedures concerning HEOA and copyrighted material are published on the University’s web site. If the University receives a complaint that a user is redistributing copyrighted material, the user’s Internet access will be blocked until the complaint is resolved. If the University receives continued complaints about a single user, the user’s Internet access will be blocked and they’ll be referred to the University disciplinary system for appropriate action.
Alternative Sources for Material
There are many legal sources to obtain copyrighted material such as music and movies. They have a wide range of business models; some are free and some charge a nominal fee. The Motion Picture Association of America (www.mpaa.org) maintains an up-to-date list of legal sources for this material.
Review Effectiveness
Beginning in 2012-2013 and periodically thereafter GCSU staff will survey faculty, staff, and students to assess the extent to which our anti-piracy messages are reaching them.
IT Research Resources
IT organization memberships
Georgia College faculty, staff, and students have access to privileged research, professional development, and other opportunities through campus membership and/or subscription to IT-related groups.
EDUCAUSE
EDUCAUSE is a nonprofit association whose mission is to advance higher education by promoting the intelligent use of information technology. EDUCAUSE programs include professional development activities, print and electronic publications, strategic policy initiatives, research, awards for leadership and exemplary practices, and a wealth of online information services. These resources and activities are available to all interested employees at EDUCAUSE member organizations, including Georgia College. Many EDUCAUSE resources (including ECAR reports) are available to the public on the EDUCAUSE website.
LinkedIn Learning
LinkedIn Learning, formerly known as Lynda.com, is an instructional video library designed to train people on the latest technology, business, leadership, and personal productivity and development skills. As faculty, staff, and students of Georgia College, you have access to a wide variety of courses that can lead to Certificates of Completion and Competency Badges that you can display on your personal LinkedIn site. LinkedIn Learning can be access by clicking on the link provided in My GCSU or by logging in here.
Microsoft OneDrive
Microsoft OneDrive is a safe, reliable, and convenient file storage tool. OneDrive allows you to access your files on any device from anywhere, even off campus. You can access OneDrive via your computer’s File Explorer/Finder, desktop app, a web browser, or a smartphone app. Once you set up the sync on your computer, OneDrive will back up your Desktop, Documents, and Pictures folder automatically, so your files are kept safe and accessible to you. This makes moving to a different computer a breeze. You can also use the sync feature on multiple devices at once, for example, on your office computer and a portable device. Follow the instructions below for setting up sync to ensure your files are properly backed up, then read on to learn all the ways you can access OneDrive.
Microsoft OneDrive Instructions
Microsoft Teams
Microsoft Teams Meetings
Microsoft Teams is a group of collaboration software that can be used to help teams work together remotely. With Teams you can easily join or host an online meeting. In the meeting you can share your screen, chat through voice, video, or text. You can divide into groups, send files, record, and transcribe the meeting. You can create Teams and Channels within a team for group work.
Using the Teams App
1. Open the Teams App.
2. Sign in with your GC e-mail address and Unify password.
3. Authenticate using DUO.
Getting started with Microsoft Teams
Introduction to Teams
What is Microsoft Teams
Microsoft Teams Sites
Microsoft Teams is a great alternative —or addition—to a department network share, often called “the Z drive” or “GC Files”. Similar to a network share, creating a team allows for sharing files within your department. Users can sync Teams files with their computer, so they can view and modify the files locally, and changes made to files are reflected globally. Note: using Teams in this way is different from SharePoint.
Microsoft Teams Site Instructions
Password Reset - Microsoft SSPR
What’s new?
It is now easier than ever for you to manage your GCSU account password, which gives access to Unify and Microsoft products. The new password reset system, Microsoft Self-Service Password Reset, or SSPR for short, allows you to change, reset, and unlock your password yourself.
The next time you log into a Microsoft product with your GCSU account (e.g., Outlook email), you may be redirected to a “More information required” page that asks you to set up authentication via your mobile phone, email, and/or security questions. Rest assured; this is a valid request. Please complete the SSPR registration by providing the information requested.
What do you need to do?
Set up additional authentication methods for your GCSU account through Microsoft if you have not previously done so. We recommend using at least 2 different methods. See the instructions below for details.
Need assistance?
If you have any questions or need assistance with your account, submit an IT Help desk ticket.
Microsoft SSPR Instructions
Personal Purchases
Personal Software Purchases (Non-University Machines)
Shop education pricing and special warranty bundles with Dell (under Exclusive Deals) and Apple
Processor: This is like the engine in a car. The more powerful, the more your device can handle. The average user will not need the high-end processors because they will most likely never use it to its full potential. You will notice different generations of processors. One way to future-proof yourself is to get a newer generation processor.
You might hear or read about the number of Cores in the processor. These are like silos for information pass. Dual or quad cores will suffice for the average user.
Storage/Hard drive: This is where your files (documents, pictures, projects) are stored on the hard drive. Much like the storage on your phone, you can fill your laptop. Most Word or Excel documents will not take up much room but pictures and videos will. Keep those things in mind when deciding how much storage you need. We always recommend using an external hard drive or cloud storage to back up your files. This can free up space on your laptop as well as provide secondary copies in case of device failure.
- SSD vs HDD
- HDDs are an older storage technology that use spinning disks to read/write data. SSDs are faster and more power-efficient than HDDs. HDDs are priced lower, but SSD prices are dropping.
RAM/ Memory: RAM is the multitasking power of your device. The average user will be using many web bases applications ( social media, Netflix, virtual meetings ) but some majors will have more robust software they use. These would require more RAM so that performance is not slowed down.
Technology Review Requirement
Technology Review Requirement
The purchase of all GCSU technology equipment and software, regardless of the source of funds, shall be reviewed by the GCSU IT Office. Please view IT Policies and Procedures for more information.
Technology Support Services provides technology quotes for faculty and staff wishing to purchase technology for university business. As required by University System of Georgia policy, the CIO must review all technology purchases before it is processed. To receive a current quote for desktop, laptop (Dell or Apple) or to have a quote created for other technology components, please submit an IT Help Desk ticket with the details of what you wish to purchase. You will receive a response within one business day Monday - Friday. If you need to speak with someone concerning a technology quote, please contact the IT Help Desk at 478-445-7378.
Unify - Bringing IT All Together
Unify provides one location to view information and access most of the GCSU Resources. Simply login and get connected. Unify is used to share important information on services, outages and campus notices.
VoIP Classroom Technology
Voice over Internet Protocol (VoIP) telephones provide quicker resolution for technical issues in the classroom and provide immediate access to Public Safety. The phone features two buttons: IT Help Desk and Public Safety. This initiative was funded by the Student Technology Fee.
Press either the IT Help Desk or Public Safety button respectively for a speakerphone call. If you lift the handset, you will automatically be connected to the IT Help Desk. To privately contact Public Safety you will need to press the button first and then lift the handset. The dial pad is disabled as the classroom phones are in a closed system using the Georgia College network. Submit an IT Help Desk ticket or call 478-445-7378 for assistance.